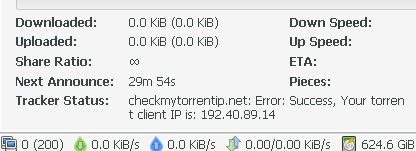
Despite supposedly having no data caps, the other day my provider interrupted my surfing with a message stating that I’d downloaded an “excessive amount” and should contact them to upgrade my plan. Interestingly, their website also doesn’t show any data caps or, for that matter, any plans for me to upgrade to.
I’m not real worried about it, but at the same time since I work full time remote I really need my intertoobs to work all the time. Then I remembered that the vacation rental we manage next door to me has internet that rarely gets used. Time to slap a wireless NIC on the server and push internet traffic through that router!
Doing so was easy. I had a halfway decent USB wireless laying around. I slapped it in, joined the next door wireless network, and then ran a route print:
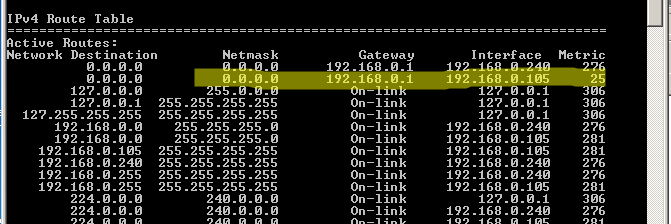
The highlighted bit is the new NIC. Above it is the wired NIC connecting the server to my local network. You want the Metric on the NIC you want internet traffic flowing through to be the lowest. Luckily mine defaulted to that. If yours doesn’t do that you can manually set the Metric by navigating to the Advanced properties of the Network Adapters:
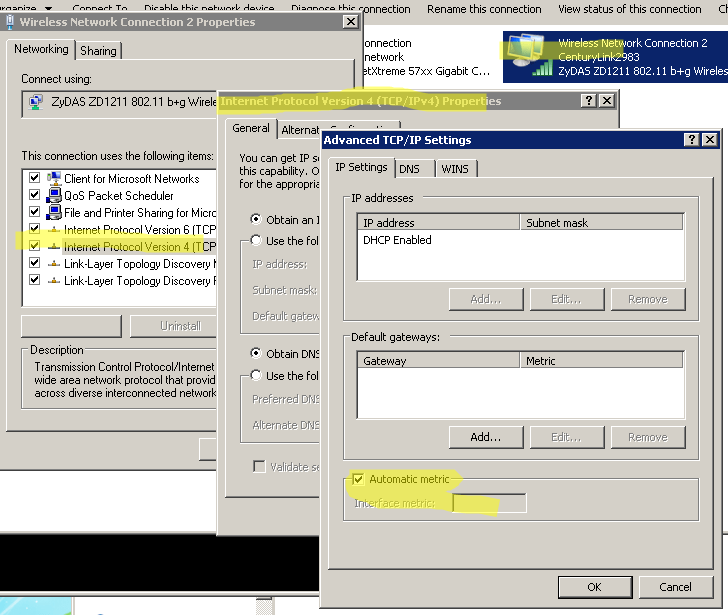
After that I simply removed the Gateway address from the properties of my wired LAN access NIC and voila – all my intertoobs were coming from next door while my LAN still had full access to my server. In order to double check I logged into my router and disabled internet traffic for the server IP address.
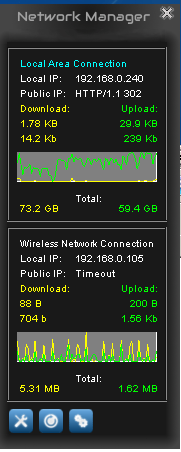
I also installed a groovy little tool called Network Manager so I can watch the traffic: