Server has a weak ephemeral Diffie-Hellman public key
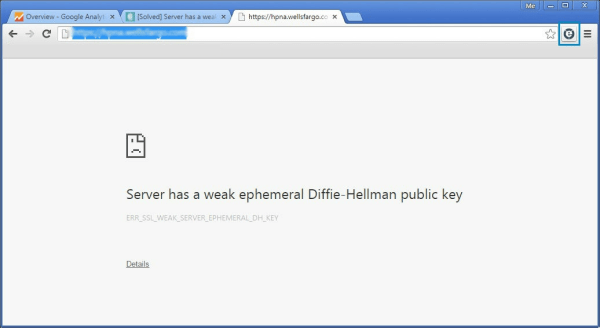
The other day my neighbor headed to a United Airlines affiliated site in Chrome to book a trip and was greeted with “Server has a weak ephemeral Diffie-Hellman public key.” Full stop. She could not continue on to the site. This is occurring because there is an attack in the wild that takes advantage of a flaw in the Transport Layer Security protocol (a fancy way of saying the supposedly secure way in which a web server communicates to your browser) in order to watch your traffic. This is called a Man in The Middle Attack. Essentially it inserts itself between you and your destination and logs your conversation. You can read more about this here.
The solution is, unfortunately, out of your hands. Your browser isn’t broken – The site you’re trying to get to is. And, as evidenced by it affecting a United Airlines site, there are some heavy hitters who are vulnerable. Any site that’s running 1024 bit or less encryption needs to upgrade to 2048 to close the hole.
But in the meantime, what if you really, really need to get to that site? I’d tell you to try to contact the site owners and tell them to get it together, but realistically that’s not so easy (can you imagine calling United’s customer service and saying to the phone jockey who answered “Hey, y’all need to upgrade your public keys on your site because currently it’s vulnerable to the Logjam attack and any decent browser isn’t allowing your site to resolve.” Yeah, you’ll get traction there). So how do you get to the site? So far there doesn’t appear to be a way to tell Chrome to continue. You can try switching from HTTPS to HTTP, but most likely you’re hitting a login page and will be forced back to HTTPS (and the error). You can, however, weaken Firefox to allow navigation on these sites. Open a new tab and in the address field enter:
|
1 |
about:config |
This opens the browser’s sekrit settings. Get past the warning, and then locate these two settings:
|
1 2 3 |
security.ssl3.dhe_rsa_aes_128_sha security.ssl3.dhe_rsa_aes_256_sha |
By default these are set to True. Change them to False and you’ll be able to hit the effected site. I STRONGLY recommend only doing this on a site you absolutely trust, and only in situations where there’s absolutely no other recourse, and I recommend changing these back to True as soon as you’re done on that site.

